Holy shit, the bootlicking and mental gymnastics in the article’s comments:
- Phones are good now! You don’t need custom ROMs!
- If you got nothing to hide you will use a stock phone!
- No average person loads custom ROMs, it’s a nerd thing!
Talking about rooting and custom ROMs is so frustrating because most of the replies are always like this.
“baCk iN mY dAy I UseD to RoOt mY gALaXy s2 bUt pHoNeS aRE sO GoOd tOdAy iTs pOinTlEsS nOw”
Motherfucker, we’re starting to not even be able to have full access to our own filesystem and Android gets more restrictive each year for alleged security reasons and you want to tell me this shit is not necessary anymore???Lemmy is potentially the first place where people actually fucking get it.
“baCk iN mY dAy I UseD to RoOt mY gALaXy s2 bUt pHoNeS aRE sO GoOd tOdAy iTs pOinTlEsS nOw”
Fucking lmao, I remember people saying that a decade ago when I had my Nexus 6P.
The 6P was such a great phone, and perhaps the following Nexus 7 was the peak of Google phones. Those were the days.
Nexus 6P was the very last Nexus device. The OG Pixel came out the following year, in 2016. I happen to have both devices, they are currently sitting on my desk, both loaded with Lineage OS. My 6P somehow managed to retain functionality of it’s entire SD810. Still gets toasty and throttles down though, and has been through a couple batteries now.
The Nexus 7 was a tablet from 2012. Damn fine tablet.
Ah, I only ever had the seven because I didn’t have a smart phone those days, and I assumed they released a phone with that number as well.
Oddly enough, the 6P is technically the 7th gen Nexus, since it came after 2014’s Nexus 6… ¯\_(ツ)_/¯
I mean its kinda true. The biggest draw to custom roms back in the day was adding features that either weren’t available at all or only on limited devices.
Even before google started locking shit down tight custom roms were dying because they had less and less to differentiate themselves from both each other and official android.
Now of course we’ve basically come full circle. We are losing wanted/needed features for “security” but shits so locked down custom roms can’t provide us with those features. :(
Just try asking about rooting in the GraoheneOS Discord, and you risk getting banned.
GrapheneOS has a ton of locked down stuff they don’t want you to access. They make rooting extra hard, they don’t support compiling the OS from source, there’s still the TEE you can’t access even with root, and the OS filesystem is readonly to inhibit customization.
GrapheneOS promotes “verified boot” that stops you from doing many important things.
they don’t support compiling the OS from source
They literally have a whole instruction page for it on their official website: https://grapheneos.org/build
What they don’t support is making modifications to GrapheneOS, compiling it, and then still calling it GrapheneOS. It’s not. You changed it, so it’s something else. It’s your own fork of GrapheneOS, so you should name it accordingly.
there’s still the TEE you can’t access even with root
Uh that’s by design? Do you even understand the purpose of a secure element and trusted execution environment, and how they work?
and the OS filesystem is readonly to inhibit customization
It’s read-only for security reasons. This is the default AOSP behavior. iOS/iPadOS and macOS handle this very similarly. This is the industry standard for secure devices. If you want to make modifications, the code is open source, you can freely modify the OS, compile it, sign it with your own keys and use it with full verified boot enabled.
GrapheneOS promotes “verified boot” that stops you from doing many important things.
Verified boot is a built in feature of AOSP. https://source.android.com/docs/security/features/verifiedboot
They literally have a whole instruction page for it on their official website: https://grapheneos.org/build
I’ve asked, and they don’t support you at all after you build it. You can’t get updates or packages from GrapheneOS. Compare to Debian, Ubuntu, RHEL, etc., where you can compile your own newer package, install it, even replace core operating system components, and then seamlessly upgrade to the OS vendor’s version when they catch up.
What they don’t support is making modifications to GrapheneOS, compiling it, and then still calling it GrapheneOS. It’s not. You changed it, so it’s something else. It’s your own fork of GrapheneOS, so you should name it accordingly.
Even if you don’t modify it, they tell you not to call it GrapheneOS, and don’t offer any way to install patches, besides building it again.
Uh that’s by design? Do you even understand the purpose of a secure element and trusted execution environment, and how they work?
Yes, I understand it. I’ve opposed TPM from the start, and this is just TPM for Android. I don’t want a device that keeps secrets from me. I do want comprehensive backups, including all cryptographic keys. I should be able to access the TEE from my authenticated PC over SSH.
I’m fully aware that Widevine won’t run on a device where the owner has control over the whole device.
The code is open source, you can freely modify the OS, compile it, sign it with your own keys…
I don’t have the resources to do this (PC nor effort). They recommend 100GB+ storage and 32GB RAM for building it, and you seemingly can’t do it incrementally, since you have to flash an entire operating system at a time. I want to modify one file, like the call recording xml file. (That file is from a previous operating system I had, but I can’t provide an example of niche cases like that for GrapheneOS, because I only ever used GrapheneOS for a few days, so I don’t know what kind of small modifications I would want to make.)
Compare to Debian, Ubuntu, RHEL, etc., where you can compile your own newer package, install it
None of these operating systems have Verified Boot. Desktop systems are inherently less secure than mobile devices.
even replace core operating system components
Don’t you see the problem there?
and then seamlessly upgrade to the OS vendor’s version when they catch up.
That’s not true either. Swapping out random parts of the OS will certainly lead to breakage and dependency hell in your package manager (unless you just replace files without using the package manager, which might make all of this even worse).
and don’t offer any way to install patches, besides building it again
Normal Android behavior. This will be the case for ANY Android-based OS with Verified Boot enabled.
and this is just TPM for Android
This isn’t comparable to TPM at all. TPM is a very insecure way of providing a hardware keystore. It can easily be bypassed. Here’s a demonstration of that https://www.youtube.com/watch?v=wTl4vEednkQ
I’ve opposed TPM from the start
TPM in desktop machines neither really provides a benefit, nor does it inconvenience the user. I’ve also opposed to it from a security perspective, since it’s misleading and makes users think that it’s actually secure and comparable to proper secure elements (such as the Titan M2, Apple Secure Enclave Processor, or the Qualcom SPU), while it really isn’t.
I don’t want a device that keeps secrets from me.
It’s not keeping secrets from you, the secure keystore is keeping cryptographic secrets away from attackers. Only you can use the cryptographic secrets from the secure element, by combining them with your PIN/passphrase (in a key derivation function) to derive the keys used for full disk encryption. Without a secure element that safely guards these secrets and throttles unlock attempts, attackers like law enforcement agencies can easily brute force your 6 digit PIN and gain full access to your device, including all of your data. The iPhone 11 was the last iPhone generation without a proper secure element. A 6 digit passcode was also bypassed on the iPhone 11 Pro Max, just a few months after its release. https://appleinsider.com/articles/20/01/15/fbi-reportedly-accessed-locked-iphone-11-pro-max-with-graykey-third-party-tool
This hasn’t been possible anymore since the iPhone 12, which was released with the Secure Enclave Processor. This is even confirmed by leaked internal documents from forensics companies, such as Cellebrite: https://discuss.grapheneos.org/d/14344-cellebrite-premium-july-2024-documentation
Specifically, I recommend looking at this chart:
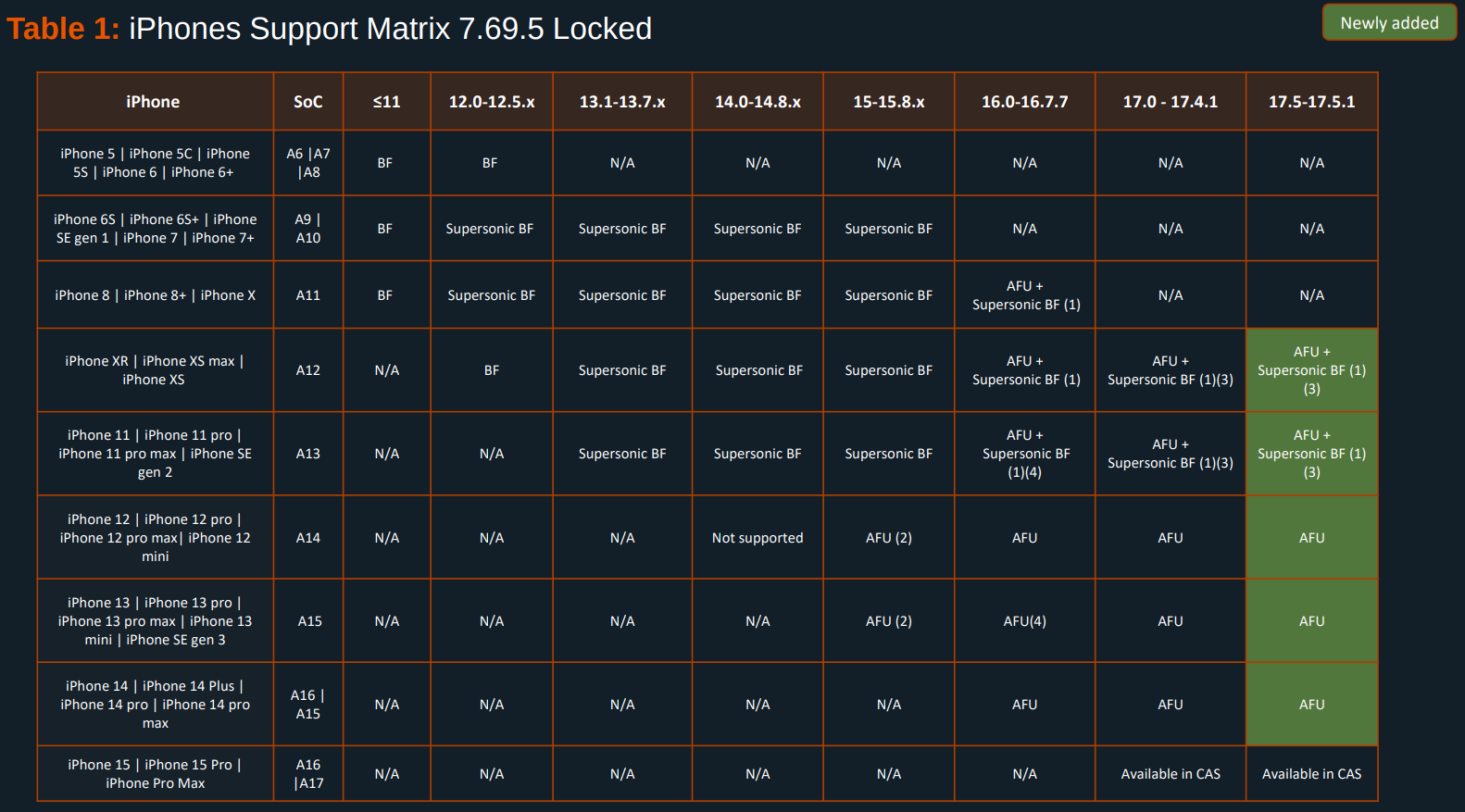
It clearly shows that data cannot be extracted from iPhones with secure elements, unless the device is in the AFU state, meaning that the encryption keys are kept in memory.
I do want comprehensive backups, including all cryptographic keys.
Having a secure element to isolate keys there doesn’t make sense if you can just export them. The security of those keys cannot be guaranteed anymore, once they’re outside of the secure hardware keystore. This is not unique to Android/mobile devices. Look at U2F hardware security tokens, such as the YubiKey or NitroKey. You can’t export your keys there either, which is by design, and it’s a good thing.
I’m fully aware that Widevine won’t run on a device where the owner has control over the whole device.
This has nothing to do with Widevine. The vast majority of Android devices currently on the market doesn’t have a secure element. Widevine still works on these devices.
and you seemingly can’t do it incrementally
What do you mean? Generating an incremental update .zip package and flashing it over your stock GrapheneOS installation? No, that’s certainly not gonna work, due to Verified Boot verifying that the signature of the update package matches the signature of the OS that’s installed. This is a very important security feature, and prevents attackers (could just be cybercriminals, but that can also include law enforcement, intelligence agencies, etc.) from hacking into update servers and delivering mallicious updates to users. If I remember correctly, that’s how EncroChat got bugged by the French police. They hacked into the update servers that were hosted by OVH, and then distributed mallicious update packages, gaining access to the devices of all EncroChat users.
since you have to flash an entire operating system at a time
That is correct. Changing the signing keys requires you to unlock the bootloader, wipe the Verified boot keys, and replace them with a new set of trusted custom (i.e. non-stock) keys. Otherwise someone could just flash a mallicious OS over your current OS, while retaining all of your data. They could then use it to extract your data.
Of course you can easily make changes and install new versions incrementally, once you have installed your custom OS and signing keys to the device. Also, none of this is some crazy GrapheneOS invention, it’s the default Android Verified Boot behavior, which GrapheneOS builds upon.
Swapping out random parts of the OS will certainly lead to breakage and dependency hell in your package manager (unless you just replace files without using the package manager, which might make all of this even worse).
I’ve done it, and it works. I’ve built packages of libraries and binaries before, at higher version numbers than Debian had, and deployed them to multiple Debian sid systems. They worked. When Debian caught up, I seamlessly upgraded all 3 systems with no problems.
Even in the worst case scenario of dependency hell, you would be able to downgrade to the Debian supported version. But I never had to do anything like that.
I’m not going to respond to all the rest of your post, because I don’t think it will help with anything. It seems that we have very different ideas about device ownership.
you would be able to downgrade to the Debian supported version
That’s pretty specific to fixed release distros, and it’s not gonna work on e.g. Arch Linux.
I’m not going to respond to all the rest of your post, because I don’t think it will help with anything. It seems that we have very different ideas about device ownership.
You don’t have to respond to it, I’d be happy enough if you would just acknowledge it. I too like the fact that one can tinker with Linux systems. I’ve always told people who want to study OS architecture to daily drive either Linux or one of the BSDs. They’re really fantastic operating systems for learning how computers and operating systems work. I too have built libraries and system utilities from scratch. I still wouldn’t recommend it on production systems. I built Linux from Scratch many times, and I think it’s pretty fun and informative (if you pay attention, instead of just copy-pasting the commands from the instructions).
Yet the fact remains that desktop operating systems are inherently less secure than mobile systems, which were designed with a strong focus on security from the ground up. SELinux is a pretty good example. How many desktop Linux distributions do you know, that deploy SELinux (or a comparable LSM) in enforcing mode, and with meaningful policies? Yeah, some of the mainstream distros, such as Ubuntu, Fedora and SUSE do it (sometimes with pretty weak policies), but looking at the vast majority of distros? I’d say almost none. Android on the other hand has used SELinux by default for a long time, with actual meaningful, secure policies. Btw if you’re looking for a more secure Linux OS, check out secureblue. It’s based on Fedora Atomic, and applies lots of hardening on top. Not affiliated or anything, I just think it’s a nice and secure distro.All in all, I think Production devices should be secure. You can always have a second device or that you can use to study the inner workings of an OS, or make changes to it (or in this case run GrapheneOS in the Android emulator).
I can understand them not wanting you to root since their focus is security above everything else, but that bit about not supporting compiling from source is a bit sketchy 🤨
Totally, since being able to compile from source is very much a security issue.
You can compile from source
They do provide instructions for compiling from source, they just don’t support you at all afterwards. If you compile GrapheneOS and put it on your phone, they say “you are not running GrapheneOS” at that point. Unlike Debian or Ubuntu, where every package can be replaced by a hand-compiled version, and it’s still Debian or Ubuntu.
Well yeah, because grapheneos is specifically made for security, not customiseability. Rooting your phone makes it a lot less secure, so it doesn’t seem strange to me that grapheneos doesn’t want you to.
Can you please explain how rooting adb only, not any apps, makes it less secure? Use concrete examples, not abstract.
USB attacks with things like Celebrite are within scope of GrapheneOS’s security model.
An exploited app can do more on a system that has more capabilities, simple as that.
GrapheneOS promotes “verified boot” that stops you from doing many important things.
What is your strongest example of an important thing that can’t be done on GrapheneOS because of its boot/loader security?
Comprehensive backups, which can only be done after rooting. You can do this, but only after disabling verified boot.
In theory Seedvault covers this. In practice…well I dunno, ask me again when I get my next phone. I’ve not had the opportunity to properly test it.
Some apps resist being backed up. “android:allowBackup=false” was one way. Apparently that can be overridden, but there are other ways apps can resist backup that can’t be overridden. It’s not clear what those are, but some of my apps definitely aren’t being backed up by Seedvault, even though they aren’t using keystore.
The apps using keystore can only ever be backed up by installing a backdoor in the TEE.
No average person
I hate this line of reasoning in all facets of life. And it does seem to appear in all facets of life.
Nobody is average in every way. If we accept that it’s okay for every goddam thing to suit only the “average”, and to hell with everyone else, then nobody will happy in more than ~3-5 aspects of their life.
Yea. Why are there so many sizes of clothes anyway? The average person doesn’t need pants with a 44 inch waist. And so many food options? The average person doesn’t need anything more than nutrient rich gruel.
Dick longer than 5.5 inches? Snip snip!
It’s not simply the average person it’s most people that don’t need this. For most people a custom rom adds nothing, most people barely change their wallpaper.
Well then let’s flip that right around then: if “most people” never do it, why the fuck should they spend the energy to ban it?
The difference between “average person” and “most people” is beside the point. It doesn’t really matter if we’re talking about 1 standard deviation from median or 3. Edge cases matter. Outliers matter. Choice matters. People matter.
Isn’t this more of a way to reduce the energy to support it instead of the opposite? I’m not in favor of removing it, but I understand the reason.
I think it’s the opposite. It takes work to implement restrictions. And they they’re presumably going to need ongoing work to patch workarounds. The restrictions would be on top of the standard functionality. They can’t remove or simplify anything by restricting app installations.
Maybe they like authority more than android over there
I read something on masto a while back that said something like “tech companies would remove the customer if they could” and I am very quickly adopting that as true in my brain.
deleted by creator
Nothing better than people onboarding themselves and also onboarding others for you.
I really don’t get the doomsayers in this thread, all boasting about how android is secure and private – that’s bullshit. Android may be secure, and Google has a rep of doing secure stuff, but it’s hardly private, 'cos Google.
Then they go on about how you just can’t do that with regular linux. Wtf?
For the most part, mobile linux distros are adapted desktop distros and all the tools you can use on android for sandboxing et al you can use on regular linux.Are there linux distros for mobile that are on par with android? No, not at the moment and not with that attitude. Can there be? For sure, and Google’s pushing it in that direction.
If you’re gonna be doomsayers bitch about hardware drivers, that’s indeed an issue and even that, it’s, like regular linux, a matter of time until someone reverse engineers them.
Mobile phones are not secure. By design
Show me a better Sandbox than the one for android apps.
QubesOS.
How usable is it in comparison to Android? Not usable. Heavy hardware and skill requirements.
Flatpak tries to be like Android app on Linux, but is not that advanced like it.
Flatpak is a security nightmare. again, stop focusing on just sandboxing and look at the whole.
It has potential. Of course Android is much better. But In comparison to other Linux application formats its better.
I mean its pretty fundamentally broken. Seems the devs don’t care about security. Better to use something like apt
Lol that’s worthless when I can unlock your phone because you use a short passphrase
Everyone can decide on the length of their passphrase according to their threadmodell.
If you use a >50 character passphrase for your phone, its no longer useful as a phone. That’s the point.
Pixels have a secure element that limit the amount of guesses an attacker could make. This isn’t available on any Linux distro by default. Also on GrapheneOS you can have a longer password for decryption and a shorter one + fingerprint for unlocking. Also a longer phone password would be more practical then an long desktop PC password. You can take the phone with you on toilet unlocked while having to lock and unlock your PC for going on the toilet.
It’s not about thief. It’s about not letting random apps access everything in system.
Lol you can make anything seem secure if you narrow security to a very narrow definition.
Phones are the most insecure devices, if you look at the big picture. They’re literally designed to be convenient. That’s the enemy of security.
This is sad. I’m clinging to my GrapheneOS Pixel 7 until it completely breaks. By then I hope there will be decent Linux phone options or I might not get another phone at all.
Google can go fuck itself. The state stock phone from most major manufacturers come in with all that increasingly intrusive spyware that you can’t uninstall or turn off should be illegal.
The government represents private interests so I think the legality is exactly where it’s intended, another fuck you to the consumer so congressional stock portfolios go up.
I wish mobile Linux was in a better state too, this sucks.
If you’re on Graphene for security, Linux mobile will be the last thing you want as the security of those devices is akin to carrying around a bootloader unlocked android with no app sandboxing. You’d be better off buying a fair phone and using iodé until they can’t develop any further.
That’s dangerously close to something Microsoft would say, like
“LiNuX is tHe LaSt ThInG you WaNt FoR sEcUrItY”
But I’ll give you the benefit of the doubt and hope you just meant that Linux mobile isn’t ready for use as a daily driver yet.
(sent from iodé)
It depends on what your requirements are. Is physical security important, or is preventing data collection more important? Not all security is the same.
I require my banking app to work.
you can use the bank website
I love that banks have tight requirements on where I can use their app, but I can visit their website from anywhere such as a public kiosk (not that you ever should!) and they’re all come on in!
fully agree, it’s ridiculous
Skill issue?
The day my Pixel 9 Pro XL came to my door, I unlocked the bootloader and rooted it. Yet, somehow, all of my banking apps (Venmo, Fidelity NB, a national bank, and a local CU) still manage to work just fine.
Depends on the bank. Hell, even McDonald’s app tries to detect this.
Ugh, the fucking McD’s app is such a pile of trash. I just now installed it to see if it got any better, and…nope. Still dogshit. No warnings about being rooted or bootloader unlocked though ¯\_(ツ)_/¯
I never implied it was, however if someone is using graphene as a way to achieve mobile security, it can generally be assumed they want said security if they switch to a different OS. Iodé and CalyxOS both support more than just pixels, and don’t do data collection, nor do they sacrifice physical security. Mobile Linux on the other hand, has very little physical security, and very poor application sandboxing compared to the aforementioned android forks. It wouldn’t make sense from a security perspective to skip over android forks directly to {postmarketos, Ubuntu touch, armbian/mobian, manjaro mobile…} unless your goal is to use a Linux phone without caring about physical security and app sandboxing (which would not make sense if you are using Graphene, and don’t want to change your threat model too much while not supporting Google.)
That’s fair. Hopefully in time mobile Linux will be comperable. I’d prefer it over Android if all else were equal. Maybe as Google keeps fucking around with users people will want to get as far away from them as possible and mobile Linux will really get going.
I agree with you, in fact the only reason I know about the security differences is because I wanted to jump ship when they started down this closing AOSP path. I found that at the current moment the security model won’t work for me, and that I’d also have to buy a new phone just to get support. I really want to try out plasma mobile though, it looks nice.
Not everyone runs dangerous proprietary apps that need sandboxing. Does my offline puzzle game need sandboxing? Firefox has its own sandbox built in.
Some people consider unlocked bootloaders a feature.
Everyone does run proprietary hardware with its own hardware vulnerabilities that could very easily be exploited and escalated without proper security. Unlocked bootloader leaves you open to very easy physical attacks. Phones batter is low and you need to charge it in a public space? You better hope no one had modified the charger with something like an RPI to silently exploit your phone. Crossing a border into a country and they suspect you’re some sort of threat? There goes all your personal information directly to their government. Not running software that updates the hardware’s proprietary software drivers? One text message and you’ve got a rootkit.
You are more than welcome to run less secure and/or insecure software. No one is telling you you can’t. If someone is on GrapheneOS however, they’re probably not using it to be on a less secure os. Most people don’t want a less secure os. I’m glad you currently have the option to do what you want, but this response to someone using a secure OS about how to stay secure didn’t really need an “um ackshually” about people who don’t want a secure os.
need to charge it in a public space? You better hope no one had modified the charger with something like an RPI to silently exploit your phone
Any secure Android device should be starting each USB session in device mode, set to charge only. It is usually not possible to change this mode without unlocking the screen. I don’t know what this has to do with sandboxing or unlocked bootloaders.
Crossing a border into a country and they suspect you’re some sort of threat?
How does this attack work? Are you saying they’d replace the operating system by using the unlocked bootloader? There are plenty of ways to prevent this with full disk encryption. Of course you need to check for modifications when you get it back, but that’s true even if you have a locked bootloader, because of hardware modifications and leaked keys.
Not running software that updates the hardware’s proprietary software drivers? One text message and you’ve got a rootkit.
In any of the open source Android distros, like LineageOS or GrapheneOS, those updates come as part of the operating system. The updater is open source, and doesn’t care whether your bootloader is locked. I assume a Linux Mobile system would be closer to Debian’s Apt system, which is also an open source updater than can install proprietary drivers, and also doesn’t care if your bootloader is locked.
didn’t really need an “um ackshually” about people who don’t want a secure os
This is pointlessly condescending.
What prevents you from sandboxing in linux? Ever heard of cgroups?
I can’t imagine someone who wants to use their phone wants to spend that time using it setting up sandboxing by hand.
There are a few for sure, but the point was the technology is there, it’s “just” a matter of implementing it.
CalyxOS didnt Pause Updates bEcAusE iTS sOoOo hArD now.
They did it because they Senior Devs are Retiring and they are switching out the Cryptographic Keys, so their Security wont be compromised.
Source: https://calyxos.org/news/2025/08/01/a-letter-to-our-community/
[CalyxOS] won’t receive any updates for the foreseeable future.
And yet, from Calyx’s own article that AA linked:
[W]e have determined that it may take up to four to six months for us to provide the level of security maintenance we aim to deliver.
AA is just fucking trash clickbait bullshit at this point.
Yeah this article read as more of a hit piece and promotion of GrapheneOS than anything else. All the “news” in the article is weeks old too.
2026, year of the Linux phone
Linux sucks on ones especially from a security and usability perspective
Edit: For those down voting, what OS do you use on your phone? Everything I’ve tried has left a lot to be desired.
Would you care to elaborate with specific examples?
Do you have examples where that isn’t the case?
Linux phones tend to just be the desktop versions of desktops adapted for a smaller screen.
Android has well built ecosystem with strong privacy and security features not really found anywhere else. The entire system focuses on least privilege with strong security isolation so even if you do download something bad it will have a hard time doing real damage.
Android is Linux, and uses regular Linux security mechanisms.
That’s not the case. Android is extensively modified in order to have sandboxed applications only and restrictive hardware permissions.
Run any executable on Linux. Likely by default it can access ~/Photos and the webcam. Android doesn’t allow that
“uses regular Linux security mechanisms” is true regardless of whether any distributions you use configure them the same way or not.
The Android platform takes advantage of the Linux user-based protection to identify and isolate app resources.
As part of the Android security model, Android uses Security-Enhanced Linux (SELinux) to enforce mandatory access control (MAC) over all processes, even processes running with root or superuser privileges (Linux capabilities).
Android also doesn’t require root for basic functionality
I’m surprised to never see Apostrophy OS being mentionned. Only comes with Punkt cellphone but it seems like a decent alternative that doesn’t use a pixel phone.
deleted by creator














